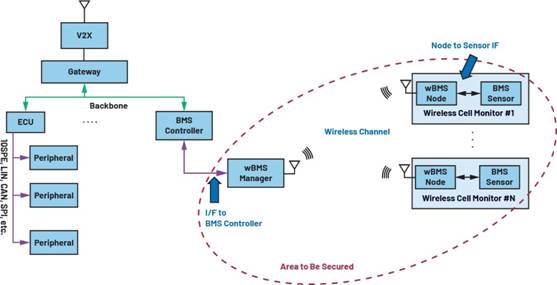
Figure 5. Threat surface considerations of WBMs
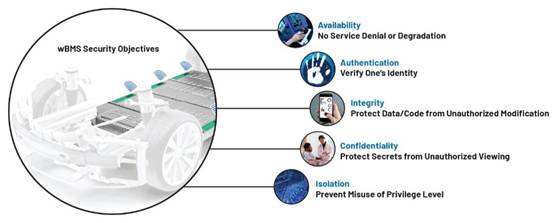
Through this exercise, you can identify the key safety objectives of the WBMs system, as shown in Figure 6. These objectives will require the implementation of mechanisms.
Figure 6. Safety objectives of WBMs
Many times, we have to answer the question: "how much are we willing to pay when we choose certain mechanisms to achieve specific security goals?" If more countermeasures are added, the overall safety situation of the product will almost certainly be improved, but the price will be very high, and it may cause unnecessary trouble to the end consumers who use the product. A common strategy is to mitigate the most likely and easiest to deploy threats. More complex attacks often target higher value assets, which may require stronger security countermeasures, but this is highly unlikely to happen, so if implemented, the return is not cost-effective.
For example, in WBMs, when the vehicle is driving on the road, it is extremely unlikely to physically tamper with IC devices to obtain access to battery data measurement, because it requires a well-trained mechanic with a deep understanding of electric vehicle batteries to operate on the components of a moving vehicle. If there are easier ways, real-life attackers may try. A common type of attack on a network system is a denial of service (DOS) attack, which makes users unable to use the product. You can create a portable wireless jammer to try to interfere with the WBMs function (difficult), but you can also deflate the tire (easy).
The process of dealing with risks by using a set of appropriate mitigation measures is called risk analysis. By measuring the impact and possibility of relevant threats before and after the introduction of appropriate countermeasures, it can be determined whether the residual risk has been reasonably minimized. The final result is that the security features are included because they are necessary and the cost is acceptable to customers.
Tara of WBMs points to two important aspects of WBMs security: device level security and wireless network security.
The first rule of any security system is "maintain key security!" This means that this is true both in devices and in the global manufacturing business. ADI‘s WBMs device security considers the hardware, IC and the underlying software on IC, and ensures that the system can be safely booted from the unalterable memory to the trusted platform for running code. All software codes must be authenticated before execution, and any on-site software update requires pre installed credentials to provide authorization. After the system is deployed into the vehicle, rollback to the previous (and possibly vulnerable) software version is prohibited. In addition, after the system is deployed, the debugging port must be locked, so as to eliminate the possibility of accessing the system through unauthorized back doors.
The network security aims to protect the wireless communication between the WBMs unit monitoring node and the network manager in the battery pack case. Security starts from joining the network, and the membership of all participating nodes must be checked. This prevents random nodes from joining the network, even if they happen to be nearby nodes. Mutual authentication of nodes communicating with the network manager in the application layer will further protect the wireless communication channel, so that man in the middle attackers cannot act as legitimate nodes to communicate with the manager, and vice versa. In addition, in order to ensure that only the target receiver can access the data, AES based encryption is used to disrupt the data and prevent information from leaking to any potential eavesdropper.
Protection key
Like all security systems, the core of security is a set of encryption algorithms and keys. ADI‘s WBMs follows NIST approved guidelines, which means that the selected algorithm and key size should be consistent with the minimum security strength of 128 bits suitable for static data protection (e.g., AES-128, SHA-256, ec-256), and use algorithms in fully tested wireless communication standards (e.g., IEEE 802.15.4).
The key used to secure the device is usually installed in the ADI manufacturing process and never leaves the IC device. These keys to ensure the security of the system are physically protected by IC devices, and unauthorized access will be blocked whether in use or not. Then, the layered key framework saves all application layer keys as encrypted binary large objects (blobs) in nonvolatile memory for protection, including those used in network security.
In order to facilitate mutual authentication among nodes in the network, ADI‘s WBMs places a unique public key pair and a signed public key certificate into each WBMs node during manufacturing. By signing the certificate, the node can verify that it is communicating with another legal ADI node and a valid network member, and the unique public key pair is used by the node in the key protocol scheme to establish a secure communication channel with another node or BMS controller. One advantage of this method is that the WBMs installation is easier, and there is no need for a secure installation environment, because nodes are set to automatically handle network security after deployment.
In contrast, the previous scheme of establishing a secure channel using a pre shared key usually required a secure installation environment and an installer to manually write the key value of the communication endpoint. In order to simplify and reduce the cost of handling the key distribution problem, assigning a default public network key to all nodes in the network is usually a shortcut adopted by many people. This often leads to the disaster of "one crash, the whole crash", which must be taken as a warning.
With the expansion of production scale, car manufacturers need to be able to use the same WBMs with different numbers of wireless nodes for different electric vehicle platforms and install them in different safe manufacturing or maintenance sites. ADI tends to use distributed key methods to reduce the complexity of overall key management.
conclusion
Only by ensuring the security from devices to networks in the whole life cycle of electric vehicle batteries can all the advantages of WBMs technology be realized. In view of this, safety requires a system level design concept covering processes and products.
ADI anticipates the core network security problems solved by ISO / SAE 21434 standard during the draft period, and adopts relevant countermeasures in the design and development process of WBMs. At present, ADI is one of the first technology suppliers to achieve ISO / SAE 21434 compliance in terms of policies and processes, and ADI WBMs technology is receiving the highest network security level certification.